Warning
This document is current with effect from the date shown on the cover page. As the International Mine Action Standards (IMAS) are subject to regular review and revision, users should consult the IMAS project website in order to verify its status at (http://www.mineactionstandards.org/, or through the UNMAS website at http://www.mineaction.org).
Copyright notice
The International Mine Action Standards (IMAS) are owned, controlled and copyrighted by the United Nations. None of the materials provided in IMAS may be used, reproduced or disseminated, in whole or in part, in any form or by any means, without prior written permission from the United Nations acting through the United Nations Mine Action Service (UNMAS), except as set out below. None of the materials in IMAS are to be sold.
The use, reproduction or re-dissemination of IMAS by third parties, in whole or in part, is permitted provided that the United Nations is appropriately attributed and provided also that such use, reproduction or redissemination is not for commercial purposes. The United Nations may be attributed by the placement of the following text: Used and reproduced with permission of the United Nations.
Director
United Nations Mine Action Service (UNMAS)
1 United Nations Plaza New York,
NY 10017
USA
E-mail: mineaction@un.org
Telephone: +1 (212) 963 0691
Website: www.mineactionstandards.org
Foreword
Management practices and operational procedures for mine action are constantly evolving. Improvements are made, and changes are required, to enhance safety and productivity. Changes may come from the introduction of new technology, in response to a new explosive ordnance (EO) threat, and from field experience and lessons learned in other mine action projects and programmes. This experience and lessons learned should be shared in a timely manner.
Technical Notes for Mine Action (TNMAs) provide a forum to share experience and lessons learned by collecting, collating and publishing technical information on important, topical themes, particularly those relating to safety and productivity. TNMAs complement the broader issues and principles addressed in International Mine Action Standards (IMAS).
The preparation of TNMAs follows a rapid production and approval process. They draw on practical experience and publicly available information. Over time, some TNMAs may be “promoted” to become full IMAS standards, while others may be withdrawn if no longer relevant or if superseded by more up-to-date information.
TNMAs are neither legal documents nor IMAS. There is no legal requirement to accept the advice provided in a TNMA. They are purely advisory and are designed solely to supplement technical knowledge or to provide further guidance on the application of IMAS. TNMAs are published on the IMAS website at www.mineactionstandards.org.
Introduction
While, over the past decades, the mine action community has taken major steps towards professionalizing explosive ordnance risk education (EORE), the increased use of improvised explosive devices (IEDs) affecting civilians poses specific challenges for EORE. The principles and guidance provided for the effective assessment, planning, implementation, management, monitoring, and evaluation of EORE described in IMAS 12.10 also apply to risk education for improvised explosive devices (IED RE). However, the latter may require further considerations.
Some considerations relate to the improvised nature of IEDs, their design and the novel ways in which they can be employed. Unlike other explosive ordnance (EO), IEDs are generally more difficult to recognize given the variety of components, designs, emplacements, concealment and employment, and the fact that they may look like harmless everyday objects. These characteristics may complicate the design of EORE messages and supporting materials, and the choice of methods for EORE delivery, that will effectively and efficiently support behaviour change in affected populations.
Other considerations refer to the extent to which the environment permits EORE interventions. Although the question is not unique to IEDs, it is often the case that contexts with IED contamination are non-permissive environments. In these cases, IED RE interventions can be perceived by armed groups or armed forces employing IEDs as an undue interference or as taking sides in a conflict. The improvised nature of IEDs may also indicate their attribution to one or more specific armed groups or forces. Delivering EORE in such contexts can result in additional risks to intended beneficiaries, EORE operators and teams. The decision as to whether and how IED RE can be delivered without resulting in protection risks for the beneficiaries (that is, risk of reprisals, forced displacement, stigmatization, etc.), requires EORE teams and operators to undertake a thorough context analysis sensitive to conflict and to diversity factors. such as age, gender and disability, as well as the implementation of a risk management approach. This supplementary attention is necessary to ensure that risks to the intended beneficiaries, EORE operators and teams are adequately identified, assessed and treated.
Whereas humanitarian clearance of EO may require a cessation of the considered conflict, EORE applies as a legal obligation to protect civilians as per international humanitarian law and international human rights law (see IMAS 12.10, 4.2). The delivery of EORE can even ultimately facilitate the acceptance of survey and clearance operations.
1 Scope
This Technical Note for Mine Action (TNMA) is primarily concerned with the provision of risk education for IEDs (IED RE) to the local population in affected countries.
This TNMA is intended to provide guidance on additional factors to be considered when designing, planning and conducting IED RE. It is not intended to be a replacement for existing standards for EORE, such as IMAS 12.10. Rather, it is considered complementary to the general principles and guidance set out in IMAS 12.10, and used as guidance to address the particular factors that may be present in places where IEDs present a threat to communities.
In addition to the principles and guidance outlined in IMAS 12.10, this TNMA provides guidance on the design of the messaging and supporting materials for the development of IED RE. Building on the principles established for risk management in IMAS 07.14, this TNMA also provides guidance on the management of specific risks to the intended beneficiaries, EORE teams and operators.
While it is not primarily intended for the provision of safety and security training to the staff of humanitarian organizations, some of the principles set out in this TNMA may be of use to organizations wishing to provide appropriate advice to their own personnel.
2 Normative references
A list of normative references is given in Annex A. Normative references are important documents to which reference is made in this technical note and which form part of the provisions of this technical note.
3 Terms and definitions
A complete glossary of all the terms, definitions and abbreviations used in the International Mine Action Standards (IMAS) series is given in IMAS 04.10.
In the IMAS series, the words “shall”, “should” and “may” are used to indicate the intended degree of compliance:
- “shall” is used to indicate requirements, methods or specifications that are to be applied in order to conform to the standard. This term is not used in TNMAs, as their contents are purely advisory.
- “should” is used to indicate preferred requirements, methods or specifications; and
- “may” is used to indicate a possible method or course of action.
3.1 explosive ordnance risk education
EORE
activities which seek to reduce the risk of injury from explosive ordnance by raising awareness of women, girls, boys and men in accordance with their different vulnerabilities, roles and needs, and to promote behavioural change
Note 1 to entry: Core activities include public information dissemination, education, and training.
3.2 explosive ordnance risk education operator
EORE operator
any organization, including governmental, non-governmental, civil society organizations (for example, women’s organizations, youth organizations, Red Cross and Red Crescent societies, etc.), commercial entities and military personnel (including peace-keeping forces), or practitioner, which is responsible for implementing EORE projects or tasks
Note 1 to entry: The EORE operator may be a prime contractor, subcontractor, consultant or agent.
3.3 explosive ordnance risk education team
EORE team
element of an organization, however named, that conducts one or more prescribed EORE activities, such as an EORE needs assessment, public information project, a school-based education project or a community mine action liaison project evaluation
3.4 explosive ordnance
EO
mine action’s response to the following munitions:
- mines;
- cluster munitions;
- unexploded ordnance;
- abandoned ordnance;
- booby traps;
- other devices (as defined by CCW APII);
- improvised explosive devices
Note 1 to entry: Improvised explosive devices (IEDs) meeting the definition of mines, booby-traps or other devices fall under the scope of mine action, when their clearance is undertaken for humanitarian purposes and in areas where active hostilities have ceased.
3.5 improvised explosive device
IED
device placed or fabricated in an improvised manner, incorporating explosive material, destructive, lethal, noxious, incendiary, pyrotechnic materials or chemicals designed to destroy, disfigure, distract or harass
Note 1 to entry: They may incorporate military stores but are normally devised from non-military components.
3.6 improvised
in the context of explosive ordnance, improvised is taken to refer to the design, construction and or emplacement of an item of EO. Such items of explosive ordnance, or components thereof, that are made from materials available at hand and have one or more of the following characteristics:
- not subject to quality control during manufacture;
- use components not in their original design purpose;
- employed in a manner or a purpose that was not intended in its design.
3.7 booby-trap
any device or material which is designed, constructed or adapted to kill or injure, and which functions unexpectedly when a person disturbs or approaches an apparently harmless object or performs an apparently safe act
Note 1 to entry: For the purpose of this TNMA, only explosive booby-traps are covered.
3.8 mine
munition designed to be placed under, on or near the ground or other surface area and to be exploded by the presence, proximity or contact of a person or a vehicle
3.9 anti-personnel mine
mine designed to be exploded by the presence, proximity or contact of a person and that will incapacitate, injure or kill one or more persons
3.10 other devices
manually emplaced munitions and devices, including improvised explosive devices, designed to kill, injure or damage and which are actuated manually, by remote control or automatically after a lapse of time
3.11 firing switch
component of an improvised explosive device that initiates the explosive train
3.12 non-permissive environment
<mine action> operational area during a specified time period where there is a humanitarian need, where access is not possible, or where consent is not provided by relevant stakeholders, preventing mine action activities to take place according to the humanitarian principles and within the framework of international humanitarian law
Note 1 to entry: This is the opposite of a permissive environment.
3.13 permissive environment
<mine action> operational area during a specified time period where there is a humanitarian need, where access remains possible, and where consent is provided by relevant stakeholders, allowing mine action activities to take place according to the humanitarian principles and within the framework of international humanitarian law
Note 1 to entry: This is the opposite of non-permissive environment.
3.14 risk assessment
overall process comprising a risk analysis and a risk evaluation
3.15 risk analysis
systematic use of available information to identify hazards and to estimate the risk
3.16 risk evaluation
process based on risk analysis to determine whether the tolerable risk has been exceeded
3.17 risk treatment / risk mitigation / risk reduction
selection and implementation of options for addressing risk
Note 1 to entry: The terms ‘risk treatment’, ‘risk mitigation’ and ‘risk reduction’ are synonyms.
4 Conflict sensitivity and “do no harm”
For the purpose of this TNMA, conflict sensitivity is understood as the ability of an organization to understand the context it operates in, the interaction between its intervention and that context, and to act accordingly in order to minimize negative impacts and maximize positive impact on the conflict.1
In order to assess and treat this risk, a conflict sensitive analysis of the environment is required to support a risk management approach.
As stated in IMAS 12.10, 4.1: “Owing to the nature of the contexts that they work in, EORE operators are required to work in a conflict-sensitive manner and to take utmost care not to put the community they work in and the EORE staff, other humanitarian partners and other partners at risk of harm or hardship as a consequence of their interventions. EORE is delivered in line with the core humanitarian principles of humanity, neutrality, impartiality and independence.”
As stated in IMAS 12.10, 4.3.5: “All EORE operations should take a conflict-sensitive approach and be implemented in line with the principles of “do no harm””, as some activities could potentially cause unintentional harm to beneficiaries, communities or personnel.
5 IED under international legal obligations to provide EORE
As reminded in IMAS 12.10, 4.2, certain international treaties impose legal obligations on States Parties to provide EORE. The following are particularly relevant for this TNMA: the Anti-Personnel Mine Ban Convention (APMBC) and the Convention on Certain Conventional Weapons Amended Protocol II (CCW APII) on Prohibitions or Restrictions on the Use of Mines, Booby-Traps and Other Devices technically.
The definition of mines, IEDs and booby-traps can overlap as shown in Figure 1.
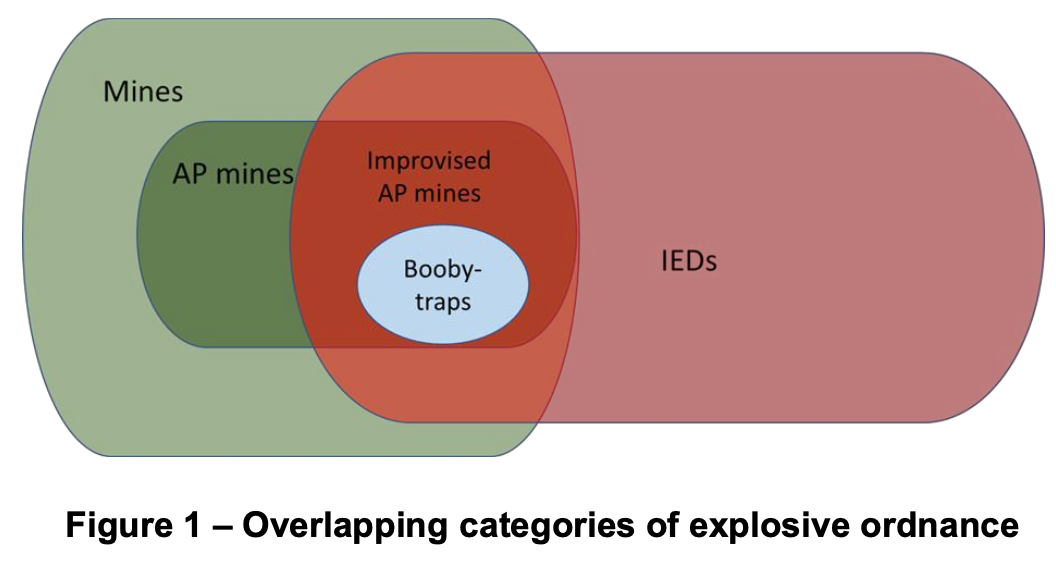
A given EO may correspond to several categories. These overlapping categories illustrate the ways in which some IEDs will fall under the APMBC and some under the CCW, obligating the States Parties to provide IED RE.
The relevance of the international treaties to the obligation to provide risk education further depends on three main factors:
- the nature of the explosive device, in particular the firing switch and the method of emplacements (for example, manual emplacement of an explosive device actuated by remote control);
- the activity of the victim or its interaction with explosive ordnance (for example, performing an apparently safe act, a daily act of living);
- the nature of the location (for example, a civilian object).
Below are some examples:
- Explosive ordnance that are actuated due to the presence, proximity or contact of a person fall under the definition of a mine regardless of their improvised nature. Such explosive ordnance is subject to EORE under the APMBC.
- Explosive ordnance that are deliberately placed to cause direct victims when an apparently harmless object is disturbed, or a normally safe act is performed fall under the definition of a booby-trap under CCW APII.
They also fall under the definition of an anti-personnel landmine under the APMBC. Such explosive ordnance is subject to EORE.
- IEDs that are manually emplaced, designed to kill, injure or damage, and which are actuated manually, by remote control or automatically after a lapse of time fall under the definition of other devices as per CCW APII. If such explosive devices are directed against civilians or have the potential to result in incidental harm to civilians, such IEDs may be subject to EORE according to CCW APII. For example, an IED emplaced in a vehicle that is driven to detonate against civilians can fall under this category.
To determine if IEDs fall under relevant international treaties in a given context, it is essential to conduct an analysis of the threat to civilians. In most cases, the analysis is based on past incidents. Accessing data directly indicating the type of explosive ordnance, especially, the type of firing switch is not always possible or consistent. In addition to information regarding the technical nature of the IED, collecting data on the circumstances of the incidents – for example, what was the activity of the victim at that moment, were they on foot or on a vehicle – can help to determine whether the explosive ordnance falls under one of the above categories. In addition, in the case of “other devices”, the technical nature of a firing switch, for example a command wire or a timer, is not sufficient to determine whether it falls under the obligation to deliver EORE. Data should demonstrate that civilians are targeted or are at risk of incidental damage.
Beyond the obligations of State Parties under the above-mentioned treaties, during armed conflicts regulated by the international humanitarian law, civilians and civilian objects are protected under the principle of distinction. It is the right of civilians to be protected from EO that cause them harm. If civilians are victims of EO, be it due to lack or absence of discrimination, or deliberate targeting, they have a right to receive specific risk education.
The national mine action authority (NMAA), or the organization acting on its behalf, should facilitate the access to such data. In particular, the NMAA should facilitate the exchange of information between organizations conducting clearance and disposal of IEDs and EORE operators. It is not the role of EORE operators and teams to collect and analyse physical technical data. In no case should they try to do so.
6 Design of messaging and material specific to IEDs
6.1 General
National authorities and EORE operators should base their projects on an EORE needs assessment. The purpose of an EORE needs assessment is to:
- identify, analyse and prioritize the local EO risks;
- assess the capacities and vulnerabilities of the women, girls, boys and men in the affected communities and other stakeholders; and
- determine the options for conducting EORE (see IMAS 12.10, Clause 5).
National authorities and EORE operators should gather sufficient information to:
- gain as accurate as possible an understanding of the extent of the EO threat and its impact;
- understand the prevalence/scale of unsafe behaviour; and
- understand the reasons for risk taking (see IMAS 12.10, 4.3.3).
This information should help to determine the location of hazardous areas and the impact and threats posed by EO on the civilian population. This is essential to raise awareness of the risk and to promote safer behaviour. As with any EO and in line with IMAS 12.10, IED RE operators and teams should design their messaging around promoting safe behaviours and addressing barriers to adopting these behaviours. It should take into account gender, age, disability, socio-economic status and other relevant diversity factors identified during the needs assessment.
In IMAS 07.14 Risk Management in Mine Action2 , Annex C tools to support the macro analysis and to assess the local threat are presented.
Where several operators deliver EORE, including IED RE, in the same context, they should ensure a common analysis. The NMAA or its Mine Action Center (or the organization acting on its behalf) should facilitate the access to data and information supporting this analysis. The NMAA should facilitate the exchange of information between EORE operators and organizations clearing IEDs.
Subclause 6.2 provides further guidance to raise awareness and to promote safer behaviour in contexts where IEDs affect communities.
6.2 Emphasising safer3 behaviour
6.2.1 General
The key is to promote safer behaviour based on the local characteristic of the threat and on the knowledge and behaviours of the different groups within the communities.
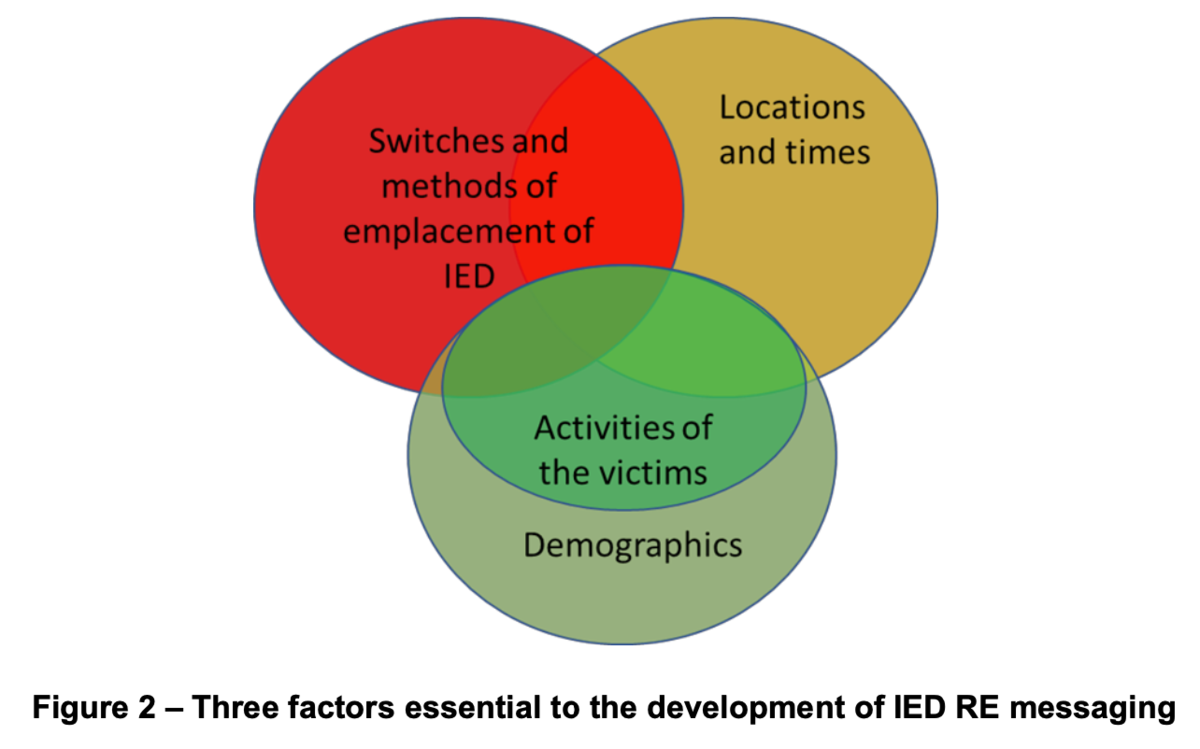
The risk from EO to persons results from the combination of three associated factors (see TNMA 07.14/01:2020, Figure 5). An explosive hazard must be present at a certain time and at a location where an activity capable of interacting with the hazard is taking place or will take place. This activity is related to demographic characteristics such as socio-economic profile, age, gender, etc.
This can be applied to IEDs as illustrated in Figure 2. The development of IED RE messaging should be based on the analysis of these factors as developed in 6.2.2 and 6.2.3. The understanding of these three factors in a given context is essential to the development of IED RE messaging.
6.2.2 Emphasizing indicators and signs
IED RE should focus on all the indicators and signs suggesting the presence of IEDs in a particular context. Based on the analysis of trends and patterns of use of IEDs in the targeted area, context and period of time, IED RE messaging should focus on providing information that emphasizes safer behaviour rather than focusing on technical components of IEDs that detract the audience from the main messaging requirement. Whereas it may be relevant to train peacekeepers or other security providers on functioning, design and components of IEDs, it is suggested that this is not the appropriate way to approach IED RE.
Messages should be clear (no use of technical jargon), simple (no information that does not contribute to the development of safer behaviour), realistic (it is based on the capacities of the beneficiaries) and practical (clear advice is proposed to the beneficiaries). EORE operators and teams should avoid overburdening the target audience with unnecessary technical information.
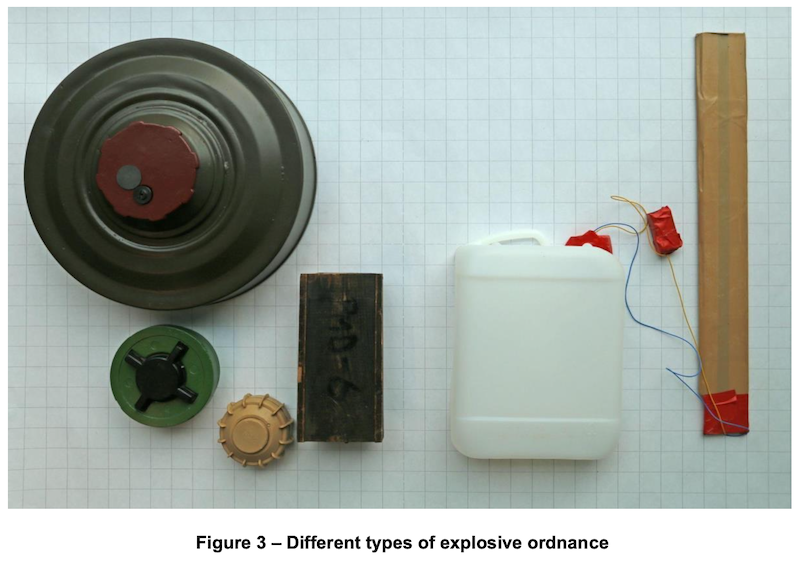
Only technical information supporting safer behaviour should be part of IED RE. In Figure 3, the mines on the left side can each be considered as one device for EORE messaging. The mine of an improvised nature on the right side has four potentially visible elements that can be explained in IED RE: a container, wires, a wrapped battery and a wrapped pressure plate. These elements are potentially emplaced in the very same place, or not. In some instances, one or several elements are partially or completely visible. Note that this picture is not an example of visual presentation for EORE. On that topic, refer to 6.3.
EORE operators should describe signs and clues indicating the potential presence of an IED in a given environment (see GICHD’s 2021 IED indicators and ground sign awareness handbook, for more details and examples of signs and clues). The identification of such clues and signs should be facilitated by the NMAA (or the organization acting on its behalf) and any humanitarian coordination system. Other actors, such as mine action organizations conducting land release operations and EOD spot tasks, may contribute to this analysis.
The analysis of events helps to determine which types of terrain features are more prone to the emplacement of IEDs. Specific points of the terrain where it is particularly advantageous to emplace an IED are also known as vulnerable points. Such analysis supports the identification by IED RE beneficiaries of terrain features that indicate the possibility of the presence of one or several IEDs.
The analysis of the design of IEDs and the methods of emplacement support the identification of signs left on the ground by the perpetrators, for example, disturbed soil or aiming marker. In addition, the components used for the design of IEDs are sometimes visible and constitute a sign such as a wire or a battery.
The analysis of trends and patterns can also support the identification of other changes to the environment that call attention to the possible presence of an IED (sometimes summarized as “presence of abnormal, absence of
normal”). It can be an object that is out of context such as a seemingly abandoned bag, container or an unknown vehicle.
The dates and times of incidents should also be analysed. Within a particular context, the likelihood of encountering IED can change during specific periods, moments or occasions. For example, this likelihood can be higher during specific hours, days, seasons or events, such as security operations.
6.2.3 Identifying at-risk behaviours
In conjunction with the above, it is essential to identify the specific vulnerabilities of the different groups within the affected communities.
Needs assessments for IED RE should also be based on reporting and analysis of incidents and information on direct victims of EO, also denoted as casualties, and with the participation of at-risk-communities. It aims to identify the most at-risk areas and periods, the most at-risk groups and the most at-risk behaviours and activities.
If feasible, setting up an ongoing injury surveillance system that includes IED-related direct victims will support this analysis. At a minimum, the collection of data should focus on direct victims. The NMAA, any organization acting on its behalf, or the humanitarian coordination system, should facilitate the collation and exchange of such information. Since patterns can evolve quickly through time and space, it is essential to monitor and analyse local trends, their incidence on the population and to review the needs assessments accordingly.
In addition to the analysis of direct victim data, EORE needs assessments should also seek to understand prevalent behaviours in the area of operations for different target groups in a manner sensitive to factors such as age, gender, disability and diversity, as well as displacement and conflict dynamics. This enables EORE operators to identify the risk of interaction between civilians and IEDs as well as with other EO. It will help to identify activities, behaviours and their drivers4 which increase this risk. In addition to the minimum data requirements,5 the NMAA and the EORE operators should focus on the circumstances leading to the events: why the victims were at the accident site, what they were doing and what were the reasons for doing this.
EORE operators may further look into specific dynamics inducing accrued risks to people. This can be the case of displacements and return dynamics.
6.3 The implications of “improvisation” for visual presentations
One of the most common methods for transmitting information in EORE is visual presentation, particularly through the use of images of EO as an aid for the recognition of dangerous objects. However, improvisation based on the builder’s imagination being a key attribute of IEDs, many items normally used on a daily basis, especially for domestic purposes, can be utilized to design IEDs, to disguise their true nature and/or to conceal them: clocks, batteries, wires, plastic containers, pressure cookers, bags, suitcase, cellphones, toys, etc. Whereas manufactured EO are most often clearly recognizable due to their shape, colour and size, this is often not the case for IEDs. Because they are often composed of objects present in daily life, there is also a risk of confusion.
Whereas images of IEDs are still needed to raise awareness, these are not sufficient to help identify an IED. Furthermore, such an approach could be counter-productive in either encouraging large numbers of false alarms, or damaging the credibility of the IED RE materials.
Nevertheless, when and where analysis shows that, within a particular context, many IEDs are of the same type or used in the same manner, it may make sense to depict the IEDs using pictures, drawings or videos focusing on the “abnormal”, for example, wires coming out of a jerrycan.
EORE operators should monitor the images they use against the evolution of the threat of IED. The images should reflect the local nature of IEDs. EORE operators should use images reflecting the local nature of IEDs. EORE operators should update the images to reflect the present nature of IEDs.
EORE operators may use images of IEDs to raise awareness but should not articulate the development of safer behaviour around images of EO only. There are alternatives to relying on pictures of items.
After gaining a thorough understanding of the circumstances under which IEDs are employed and of the local behaviours developed in 6.1, EORE operators may present images of these circumstances (similar to presentation of “mine indicators/clues”) and then provide visuals of actions to avoid such circumstances (that is, “safer behaviour” advice).
6.4 Alternatives to relying on pictures of items: other approaches
Small media (like posters and leaflets) encourage the use of pictures of items due to their size and layout. Therefore, in IED RE it is suggested to promote safer behaviour through alternative media, such as oral storytelling, songs or theatre. Storytelling can easily be combined with pictures of safer behaviour, for example. The use of radio or, at least, borrowing from radio techniques, is another variation of oral storytelling. Writers for radio inevitably have to rely on mental images in a medium which does not use pictures.
6.5 Adapting the IED RE to actual threats
Patterns of IED use are often fluid. They can be both highly localized and change rapidly in areas of concern. Messages and supporting materials can be relevant to a place and moment but less relevant in another place and through time. In order to adapt IED RE to actual risks in a given area, the NMAA and EORE operators should constantly monitor trends and review threat analysis, threat assessments and needs assessments, including ongoing injury surveillance. The NMAA, or any organization acting on its behalf, or the humanitarian coordination system, and EORE operators should constantly review these documents. They may liaise with other organizations dealing with IED to facilitate the monitoring of the threat. They should maintain the engagement with affected communities to monitor the behaviours.
Regarding supporting materials, digital and radio campaigns, where applicable, offer advantages as they allow for quick adaptation. If printed materials are used, then EORE operators should avoid printing too much surplus stock.
7 Risks related to the delivery of EORE in non-permissive environments
7.1 General
The NMAA, or organization acting on its behalf, and the EORE operators should pay special attention to messaging and risk management in the context of ongoing and protracted conflicts, whether or not they are of international nature.
In addition to the risks posed to themselves, the NMAA and the EORE operators should assess the risks of unintended adverse impact posed to the potential beneficiaries in order to carefully select the options to treat these risks.
7.2 Risks to affected communities
Three common elements of EORE messaging are:
- IED awareness and recognition. How to recognize the threat and the dangerous areas (see Clause 6).
- Promoting safer behaviour (see Clause 6 also). This is generally articulated around the following main messages:
- “Stay away from hazardous areas and suspicious objects”;
- “Do not touch, do not approach suspicious objects”;
- “Emplace warning signs to indicate the presence of suspicious objects” is sometimes included.
- Reporting.
Including a “marking” and a “reporting” element to RE can lead to risks for intended beneficiaries in environments that are not fully permissive. One key aspect of a “do no harm” approach to IED RE should include consideration of the implications to the security of local populations if they are being exhorted to mark and report EO currently in use by parties to the conflict. In particular, the NMAA and the EORE operators should assess the risk of reprisal if IED and other EO are marked or reported to authorities.
7.3 Risks to EORE (and other agency) teams
There are similar risks to the EORE operators and teams who are attempting to deliver EORE interventions, especially but not only where the “report” message is included. In such circumstances, and regardless of the type of EO, the EORE personnel (and potentially, by extension, other personnel working with this EORE operator) may also be at risk from reprisals, as it may be felt that they are taking sides with one party to the conflict.
The EORE operators and teams should carefully assess these risks. If the EORE operators consider a collaboration with local partners to relay EORE, then the EORE operators should involve these local partners in the risk assessment to inform the decision.
7.4 Managing risk to IED RE stakeholders
7.4.1 General
The circumstances that may apply in any one country, or even in any one community are very variable. Thus, it is impossible to lay down any immutable advice on the best way to apply the principle of “do no harm” and continue to provide IED RE that is effective in modifying behaviour, hence reducing the number of victims. A more detailed risk assessment process is set out in Annexes C and D. There are however a few alternatives that can be considered.
7.4.2 Modifying the marking message
Affected communities sometimes improvise markers and signs to warn the community of the presence of an EO or of a hazardous area (see IMAS 08.40 on informal marking systems). In some cases, indicating the position of IED with markers and signs can put the community at risk of reprisals. It is still vital that the information concerning the presence of IED is passed among the at-risk communities in an inclusive manner. The at-risk communities may be better placed to elaborate their own warning mechanisms with the support of EORE operators which have the technical understanding of the design of IEDs.
As part of the needs assessment and monitoring of IED RE, EORE operators should engage with at-risk communities on the issue of marking. The NMAA and EORE operators, in close coordination with at-risk communities, should assess the risk associated with improvised marking of EO and elaborate mechanisms to warn and exclude the population from hazardous areas. Such mechanisms should take into account marginalized groups to be inclusive. Security institutions and parties to the conflict may be included in the elaboration of these mechanisms.
If the contamination in the area contains EO other than IED, the NMAA and EORE operators should agree on the overall marking messaging.
7.4.3 Modifying the report message
In some circumstances the use of a confidential or anonymous reporting system might be sufficient to help with safe reporting. Alternatively, it may be appropriate to suggest that they report any such items to their own community leaders, who may be better placed to identify alternative solutions, rather than advising beneficiaries to report suspected IEDs to the security forces. Instead of formal reporting, communities may be encouraged to warn their family members, trusted neighbours and community members on the known or suspected presence of IEDs.
As part of the needs assessment and monitoring of EORE, EORE operators should engage with at-risk communities on the issue of reporting. The NMAA (or organization acting on its behalf) and EORE operators should elaborate reporting mechanisms in close coordination with at-risk communities. These reporting mechanisms should take into account marginalized groups to be inclusive. Security institutions and parties to the conflict may be included in the elaboration of reporting mechanisms.
7.4.4 Separating IED from standard EORE presentations (where applicable)
It may be appropriate to separate IED RE from other EORE messaging in conflictual contexts where IEDs are being used.
Such a decision should be informed by the analysis of the conflict. This analysis should indicate if any party to the conflict, especially parties using IEDs, would consider IED RE as contravening their objectives, being illegitimate or even directed against them. For example, in some cases, the analysis could indicate that civilians are deliberately targeted by IEDs.
As a result of such analysis, the NMAA (or organization acting on its behalf) and EORE operators may not include IED RE messaging in EORE. Alternatively, they may conduct separate IED RE messaging.
When doing so, EORE operators and teams should maintain their neutrality and not stigmatize specific sides of the conflict only, nor refer to combatants. Breaching neutrality of the messaging increases risks to the communities and to the EORE operators and teams.
In addition, EORE operators may consider not including their own names or logos in IED RE messaging. They should also confirm if donors and partnering organizations want to be visible or not. It also may be appropriate for the relevant national authority to “own” the messaging.
The analysis of the nature of IED incidents could indicate that some IEDs, such as vehicle-borne or person-borne IEDs, are used similarly to other forms of explosive weapons attacks, such as aerial bombardment or shelling. The NMAA (or organization acting on its behalf) and EORE operators may consider including specific messaging in larger programmes designed to improve preparedness, build resilience and enhance protection of civilians against explosive weapons6. Such programmes would require a thorough conflict-sensitivity analysis as described in 4 and may include diverse safety measures such as basic first aid or fire safety.
7.4.5 Use of alternative RE delivery methods
When the environment does not permit the EORE operator to directly access beneficiaries, the use of mass media campaigns and/or digital technologies may be considered. EORE operators may also consider the implementation through local partners provided that a joint risk assessment has been conducted, and that risk treatment measures are identified and accepted. Equally, such partnership should be conflict-sensitive. All these approaches have advantages and disadvantages.
In case of implementation through local partners, the NMAA (or the organization acting on its behalf) and EORE operators should ensure the transfer of competence through training.
7.4.6 Communication with parties to a conflict
In particular contexts and where appropriate, the NMAA, or the organization acting on its behalf, and/or the EORE operators may seek to communicate with parties to a conflict to gain acceptance of IED RE.
When conducting IED RE, the NMAA and EORE operators should develop clear security protocols, including guidelines on what to do if a party to the conflict questions the EORE operators and EORE teams about the activities being conducted.
8 Training requirements for EORE operators
It can be seen from these issues that there are additional training requirements for engaging in safe and effective IED RE. This additional knowledge does not replace but completes the competences needed to deliver EORE and to operate as safely as possible. Whereas the following additional training requirements are suggested as a minimum, specific circumstances may require more training. As for any EORE, there is no need to provide exhaustive and detailed technical training on IED components and construction for strict IED RE purposes. As a prerequisite, EORE teams should be thoroughly trained in the humanitarian nature of their job and the associated humanitarian principles to follow. Suggested minimum additional knowledge requirements are as follows.
-
Circumstances of use
-
Define IEDs.
-
Know how IEDs tend to be used in the affected country and in the targeted area.
-
-
IED indicators/ground sign and situational awareness
-
Explaining where IEDs are likely to be encountered.
-
Explaining signs suggesting the presence of IEDs.
-
Explaining circumstances under which IEDs are likely to be encountered.
-
-
Introduction of different types of IEDs
-
Recognize and name typical components of IEDs.
-
Break down by types of firing switch: time/victim/command.
-
Know IED acronyms (VOIED, VBIED, PBIED, etc.).
-
Describe level of technical details relevant to IED RE.
-
-
Notion of permissive/non-permissive environments
-
Explain the notions of permissive/non-permissive environment and their implications for IED RE.
-
Explain the importance of the core humanitarian principles.
-
Explain the importance of conflict-sensitivity and “do no harm”.
-
Point out similarities and differences with other forms of EORE, if relevant.
-
Explain which messages are acceptable and which are not.
-
Explain the reporting issues where these are relevant.
-
-
Risk assessment
-
Fully involve EORE teams in the risk assessment process as part of their training, so that they are comfortable with the conclusions.
-
Explain the need to be aware of their own safety and that this is a core part of the approach being taken.
-
Explain how to introduce the subject to local communities and leaders and seek local approval of the training before it is provided, especially during active hostilities.
-
Assess whether it is appropriate to implement IED RE together with other EORE interventions. See Annexes B, C and D.
-
Annex A (normative) References
The following normative documents contain provisions, which, through reference in this text, constitute provisions of this TNMA. For dated references, subsequent amendments to, or revisions of, any of these publications do not apply. However, parties to agreements based on this TNMA are encouraged to investigate the possibility of applying the most recent editions of the normative documents indicated below. For undated references, the latest edition of the normative document referred to applies.
-
IMAS 04.10, Glossary of mine action terms, definitions and abbreviations
-
IMAS 05.10, Information management for mine action
-
IMAS 07.14, Risk management in mine action
-
IMAS 08.40, Marking of explosive ordnance hazards
-
IMAS 12.10, Explosive ordnance risk education
Annex B (informative) Risk management for IED risk education
When considering the delivery of IED RE, this annex highlights specific considerations to be incorporated in risk management processes and tools described in IMAS 07.14 Risk Management in Mine Action.
This annex establishes additional guidance to assess if delivering IED RE would possibly result in accrued threats and opportunities for EORE operators and intended beneficiaries. This guidance applies to processes and tools described in IMAS 07.14, especially its Annex C Threat Analysis and a Threat Assessment in Environments Affected by IED.
It is important to conduct and review risk assessments:
-
at different levels to include the national level and the micro-level (IED RE project level);
-
periodically and at moments when there is a major change to the context.
B.2 Analysis of the (non-)permissiveness of the context of IED RE programmes B.2.1 Analysis of the conflict
Like for any EORE intervention in a conflictual context, it is essential to identify and analyse:
-
the sources of tensions, the causes and deep roots of the conflict;
-
the stage of the conflict (for example, escalating or de-escalating);
-
the actors of the conflict (for example, who they are, which are their main interests, goals or positions).
If the area affected by the presence of IED is no longer subjected to an ongoing conflict, then including IED in RE possibly represents no additional risk for the beneficiaries, EORE teams and operators.
If the area is subjected to an ongoing conflict, it is possible that the inclusion of IED RE within EORE, results in additional risks to the implementing EORE operator, EORE teams and beneficiaries. These risks include retaliation from parties to the conflict.
For a given country, it is possible that the status of the conflict differs from an area to another, that is, active in one area and finished in another area. It is also possible that the status of a conflict changes over time. Thus, the status of a conflict should be determined.
B.2.2 Analysis of IEDs
It is essential to identify and analyse the impact of IED on civilians in conjunction with:
-
their technical nature;
-
the wider context of the conflict; and
-
its actors.
It is important to determine how and why the civilian population is impacted by IEDs. For example, it is important to determine if some actors of the conflict deliberately target civilians.
Additional steps also need to be undertaken in the form of a risk assessment taking into account intended beneficiaries, EORE teams and operators. These additional steps are as follows.
B.3 Risk assessment
The above should support the assessment of risks related to the delivery of IED RE under current and local circumstances. It includes risks to:
-
EORE operators and teams;
-
intended beneficiaries;
-
partners and other stakeholders;
-
EORE programming. These risks include:
-
security risks to EORE staff, equipment and premises;
-
similar risks to partners and other stakeholders;
-
confidence of communities towards EORE operators and teams;
-
access for/to EORE.
For each risk, it is necessary to assess:
-
the likelihood, proximity and impact;
-
if these risks are tolerable;
-
appropriate risk treatment options (see Clause 6);
-
the residual risk and its tolerability for any risk treatment option.
B.4 Methodology
The above analysis should involve a combination of different methods to include the following:
-
data analysis;
-
desk research;
-
consultations with communities;
-
workshops with EORE stakeholders and other relevant actors, such as IED clearance operators. Additional methods may be employed, for example, surveys or expert interviews.
The NMAA (or the organization acting on its behalf) should involve EORE operators in the identification information requirements (see IMAS 05.10, 7.2).
Examples of detailed questions to support the risk assessment are presented in Annex D. It is recommended that the questions in Annex D be used as part of the risk assessment (and subsequent risk reviews), and the answers gained from the questionnaire then used in turn to help navigate the flow chart in Annex C.
Annex C (informative) Example of IED RE risk assessment flow chart
IMAS 07.14, Annexes B and C, provide detailed guidance on risk management tools, threat analysis and threat assessment in environments affected by IEDs. This annex proposes an application of these tools for the purpose of IED RE programming.
It is essential that products of these tools and processes are collated in a risk register, closely monitored and reviewed in a dynamic and responsive manner, especially in highly complex and fast developing environments.
It is also essential to establish clear criteria concerning the tolerability of risks for the intended beneficiaries, the EORE teams and operators.
At the level of EORE operators, these criteria may generally be well established and understood. With regard to the “do-no-harm” principle, it is essential to involve intended beneficiaries in the risk management process.
Desktop reviews of available information as well as community liaison support this process.
The first step aims to understand the context, assess the need for IED RE and determine if the environment is permissive or non-permissive.
The second step aims to determine the risks to the intended beneficiaries, EORE teams and operators if IED RE is delivered.
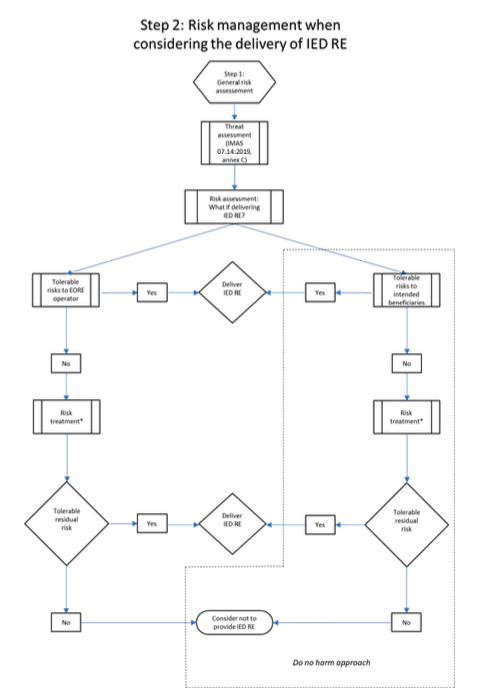
Risk treatment options include:
- avoiding the risk: for example, not undertaking EORE;
- removing the risk source: for example, through access negotiations or indirect RE methodologies; changing the likelihood: for example, separating IED from standard EORE;
- changing the consequences: for example, modifying or removing the report message;
- sharing the risk: for example, using local partners;
- accepting the risk.
Annex D (informative) Example research questions for IED RE risk assessment, and threat analysis and assessment
D.1 General
When considering the delivery of RE for IED, this annex proposes questions to be incorporated in risk management processes and tools described in IMAS 07.14, especially in its Annex C. Concerning needed data, IMAS 05.10, Annex B, provides guidance on minimum requirement, and IMAS 05.10, 7.2, provides guidance on the specification of information requirements.
D.2 Step one: The risk and threat assessment process
D.2.1 General IED situation
The following questions are intended to complement a general security/mine action briefing on the IED situation in the country.
The risk implications of engaging in IED data-collection or risk education are significant in a context where the IEDs are actively employed by parties to the conflict. Therefore, it is essential to carefully analyse available data to assess whether the IEDs are currently employed or a result of past conflict. This analysis shall be carried out at a national but also more local level as the context requires.
# | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 1.1 | How does the incidence and prevalence of IED use compare to that of other weapons? | Compile evidence on the relative importance of IEDs. This may help to ultimately balance the decision as to whether to deliver IED RE or not. | Analysis of IMSMA data, injury surveillance systems and other data collection mechanisms (for example, M&E Mechanism for the UN Mine Action Strategy; Monitoring and Reporting Mechanism on grave violations affecting children) |
| 1.2 | Which are the parties to the conflict known to use IEDs? | It is important to identify the different parties to the conflict or armed forces that use IEDs, because they will not all be using them in the same way. The subsequent analysis should be carried out keeping in mind the different parties to the conflict and how that impacts the other research questions. | Mapping of different parties to the conflict; people with knowledge (PwK) interviews; secondary data research |
| 1.3 | Why are parties to the conflict using IED? | IEDs can be used for different reasons, for example, to create terror among the local population, to challenge state control of certain areas, in cases where parties to the conflict do not have access to other weapons, as a substitute of small arms, as command-detonated devices to secure security forces positions | PwK interviews; secondary data research |
| 1.4 | Who is currently involved in efforts against IEDs? | It is important to identify who is already working to reduce the risks of IEDs. | Mapping of different state, commercial, security providers, UN and NGO actors involved in IED risk reduction. |
| 1.5 | What is the scope of their activities? | The agency should aim to supplement not duplicate activities of other actors, depending on the need. | |
| 1.6 | Are the IEDs currently used by parties to the conflict? | If parties to the conflict using IEDs consider it to be a legitimate means, they may want to oppose IED RE or to restrict IED RE. | Write up the analysis of PwK interviews and secondary research. Claims by perpetrators of IED use. |
| 1.7 | Is there any current target for the IEDs? | If there is a current target for IEDs, then they are considered an element of an ongoing conflict. | Open and non-open-sourced data, PwK interviews |
| 1.8 | Are there differences between geographic locations in-country in terms of whether the IEDs can be considered as being currently employed or remnants? | Even in the case of an ongoing conflict, it is possible to consider IED RE activities in the areas where active hostilities have ceased or remote IED RE where active hostilities are ongoing | Conflict and IED maps |
D.2.2 What is the nature of the IED threat?
Using the working definitions described previously, an analysis should be carried out to determine whether the bulk of the problem is with booby-traps or other improvised mines, or with specific types of command detonated IED (VBIED, PBIED, road-side bomb, time bomb, etc.).
| # | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 2.1 | What is the overall number of incidents involving IEDs in-country? | This should include data for all types of IED to give the scale of the problem overall. | If available, the data should be provided for IED use over time. Ideally it should be disaggregated by year to show whether IED use is increasing or decreasing. Sources of information include: open source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. |
| 2.3 | Are victim-operated IEDs designed to be antipersonnel or anti- vehicle or both? | Comparing these pieces of information with information on the direct victims will help to establish the relationship between the nature of IEDs and their impact on civilians. These pieces of information will also support the elaboration of awareness and messaging tailored according to specific risks. | Provide analysis and charts of any recent data to demonstrate the percentage of different types of devices being used. IED maps; open-source database, specialised agencies to include humanitarian ones; IMSMA data. Sources of information include open- source database, specialized agencies to include humanitarian ones, IMSMA data, UN verified data from the Monitoring and Reporting Mechanism on Grave Violations against Children in Situations of Armed Conflict, other M&E mechanisms internal incident mapping, etc. If no good quality data is available on the nature of IED use, this should be noted in the analysis. |
| 2.4 | What are the methods to deliver IEDs (emplaced or carried to the tagret)? | Comparing these pieces of information with information on the direct victims will help to establish the relationship between the nature of IEDs and their impact on civilians. These pieces of information will also support the elaboration of awareness and messaging tailored according to specific risks. | Provide analysis and charts of any recent data to demonstrate the percentage of different types of devices being used. IED maps; open-source database, specialised agencies to include humanitarian ones; IMSMA data. Sources of information include open- source database, specialized agencies to include humanitarian ones, IMSMA data, UN verified data from the Monitoring and Reporting Mechanism on Grave Violations against Children in Situations of Armed Conflict, other M&E mechanisms internal incident mapping, etc. If no good quality data is available on the nature of IED use, this should be noted in the analysis. |
| 2.5 | What is the geographical and time distribution for each of these categories? | If IEDs are used by parties to the conflict in one location, but IED remnants pose a threat in another location no longer under conflict, it may be necessary to consider different types of IED RE. The geographical and time distribution of IED can also be used to promote safer behaviours. | Provide analysis and charts of any recent data to demonstrate the percentage of different types of devices being used. IED maps; open-source database, specialised agencies to include humanitarian ones; IMSMA data. Sources of information include open- source database, specialized agencies to include humanitarian ones, IMSMA data, UN verified data from the Monitoring and Reporting Mechanism on Grave Violations against Children in Situations of Armed Conflict, other M&E mechanisms internal incident mapping, etc. If no good quality data is available on the nature of IED use, this should be noted in the analysis. |
D.2.3 What is the impact of IED on the civilian population?
| # | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 3.1 | What is the overall percentage of civilians among direct victims of IEDs? | This helps to provide evidence for the extent to which the civilian population is at risk from IEDs. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Gender and diversity analysis. |
| 3.2 | How does the number of civilian victims from IEDs compare to that of those from other weapons? | This will provide evidence of whether IEDs or other weapons have greater humanitarian impact. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Gender and diversity analysis. |
| 3.3 | For each category of IED defined in Clause 3, what is the percentage and the number of civilian direct victims? | This will support the decision concerning the delivery and the content of IED RE. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Gender and diversity analysis. |
| 3.4 | What is the geographical and time distribution for these direct victims? | The risks possibly vary from an area to another and through time. This information will support the design and the delivery of IED RE tailored according to specific risks. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Gender and diversity analysis. |
| 3.5 | Are specific groups (age, gender, disability, ethnicity, political belief and practices, language, socio- economic occupation, etc.) particularly impacted? | This will support the design and the delivery of IED RE tailored according to specific risks. Even when they are not the primary target of IED, civilians often represent the highest number of direct victims from being in the wrong place at the wrong time (“collateral damage”). The EORE operator might be able to provide IED RE in these circumstances, but additional steps also need to be undertaken to complete the risk analysis. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Gender and diversity analysis. |
| 3.6 | Are there evidence or reasonable indications of civilians being deliberately targeted with IEDs (that is, claims)? Are specific groups (age, gender, disability, ethnicity, political belief and practices, language, socio-economic occupation, etc.) particularly targeted? | This will help to determine or to assess whether parties to the conflict using IED would oppose or restrict the delivery of IED RE. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Public claims by parties to the conflict using IED, analysis of the conflict. |
| 3.7 | Why would the civilian population or specific groups of the civilian population be targeted with IEDs? | It is necessary to understand the logic or the motivation behind why one group or another is targeted. | Sources of information include: open-source database, specialized agencies to include humanitarian ones, IMSMA data, national injury surveillance systems, internal incident mapping, etc. Public claims by parties to the conflict using IED, analysis of the conflict. |
| 3.8 | What are the common scenarios in which civilians are killed or injured during IED incidents? | This helps to understand which is the primary target;
| Analysis of the conflict. |
| 3.9 | Are there any specific places where the local population are most at risk from IED attacks? Why? | In some countries where civilians are the direct targets, they will typically be most at risk in places such as markets, moto parks, restaurants, mosques, churches, etc. It is necessary to understand what these places are in the country context. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA, Injury surveillance systems, database, etc. |
| 3.10 | How do IED impact on people’s daily lives? | It is important to understand what coping strategies (if any) are already adopted | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA, Injury surveillance systems, database, etc. |
| 3.11 | What are the common behaviours of the local population if in the proximity of an IED attack? | In some instances, the behaviour of the local population in the immediate aftermath of an attack can increase their exposure to risk. For example, often people run to assist victims of an initial blast and are then caught up in a secondary blast. | |
| 3.12 | What can be done to reduce the vulnerability of the civilian population to the IED threat? | It is important to take into consideration do-no-harm principles, gather information and ideas on how this vulnerability can be reduced. It is also important to gauge interest in IED RE sessions. | Engagement with at-risk communities. |
D.2.4 Who is the intended target of IEDs?
It is important to identify and provide evidence on the primary target of IEDs as it impacts on the course of action that the EORE operator should take.
| # | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 4.1 | It is necessary to understand the logic or the motivation behind why one group or another is targeted. | It is necessary to understand the logic or the motivation behind why one group or another is targeted. | Analysis of the conflict |
| 4.2 | In complex security environments, this information supports the assessment of the risks to EORE operators and beneficiaries. | In complex security environments, this information supports the assessment of the risks to EORE operators and beneficiaries. | Sources of data include open- source databases, specialised agencies, media reports, claims. |
D.2.5 What are the common tactics of IED use?
| # | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 5.1 | What are the most common tactics used for IED attacks? | It is necessary to understand the most common tactics for IED use, for example, as part of a complex attack; VBIED parked in a crowded market; RCIED at the roadside detonated as a military vehicle passes, etc. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 5.2 | Are there any differences in tactic, depending on whom the target is? | This information will support the design of risk awareness and messaging. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 5.3 | Are there any particular places that are most commonly targeted? | It is necessary to understand if there are any specific places where people are most at risk of being killed or injured during IED attacks. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 5.4 | What are the common indicators of IEDs? | This information will support the design of risk awareness and messaging. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 5.5 | What are the common indicators of an imminent IED attack? | We need to know if there are any context-specific signs that an attack is about to take place. In some cases, these are quite distinct (for example, an empty market on market day), but in other cases they are not. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
D.2.6 What is the impact of IED on the humanitarian and development actors?
| # | Question examples | Explanation | How can this question be answered? |
|---|---|---|---|
| 6.1 | What percentage of overall IED victims are humanitarian and development actors? | This helps to provide evidence for the extent to which the humanitarian community is at risk from IEDs. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 6.2 | What are the common scenarios in which humanitarian and development actors are most at risk of IED attacks? | This helps to understand whether they are: bystanders who are killed in the initial blast; caught in gunfire following an explosion; caught in a secondary blast, etc. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 6.3 | Are there any specific places where humanitarian and development actors are most at risk of IED attacks? | In some countries where civilians are the direct targets, they will typically be most at risk in places such as restaurants, mosques, churches etc. It is necessary to understand what these places are in the country context. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 6.4 | How does the IED threat impact on the delivery of humanitarian and development assistance? | There are many possible effects, such as increased security costs, fear of attacks at distribution points. etc. It is necessary to understand from the perspective of assistance providers what those effects are. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 6.5 | To what extent is the staff of humanitarian and development organizations equipped with the knowledge and skills to work in contexts where IEDs are a significant threat? | What safety training has been given? How relevant or accurate is it? | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 6.6 | What can be done to reduce the vulnerability of humanitarian and development organizations and their staff to the IED threat? | It is important to gather information and ideas on how this vulnerability can be reduced. It is also important to gauge interest in risk education for humanitarian workers. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include open- source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
D.3 Step two: The risk evaluation process
NOTE: the conclusions drawn from this risk evaluation process will be very dependent on the EORE operator’s willingness to accept risk. These notes are for guidance only.
D.3.1 What are the risk implications of engaging in IED risk education for the EORE operator?
| # | Question examples | Explanation | How can the question be answered? |
|---|---|---|---|
| 7.1 | Who is currently involved in counter-IED efforts in-country and what are the challenges that they have faced? | It is necessary to know if other agencies involved in counter-IED have become targets for parties to the conflict because of the work that they are carrying out. If they have then the risk-implication for the EORE operator as an organization is high. | Mapping of stakeholders |
| 7.2 | In general, how will the provision of IED RE affect the EORE operator status as neutral and impartial? What could be the result of that? | Any involvement in counter-IED could be perceived as taking sides in the conflict. | Conflict analysis |
| 7.3 | How will the government perceive the involvement of the EORE operator in the provision of IED RE? | In many countries, counter-IED efforts are typically dealt with by state entities. Any effort by the EORE operator to engage in IED RE may therefore not be well received and could result in negative consequences for the organization. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include: open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 7.4 | How will security providers perceive the involvement of an international organization/NGO in the provision of IED RE? | In many countries, counter-IED efforts are typically dealt with by state entities. Any effort by the EORE operator to engage in IED RE may therefore not be well received and could result in negative consequences for the organization. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include: open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 7.5 | How will parties to the conflict perceive the involvement of an international NGO in provision of IED RE | The perception that humanitarian organizations are affiliated with the state entities counter-IED efforts would call into question the neutrality and impartiality of the humanitarian organization involved and could result in the organization and its staff being considered as legitimate targets for attack by parties to the conflict. | Provide analysis of any recent data to demonstrate the percentage of attacks against different targets. Sources of data include: open-source database, specialized agencies to include humanitarian ones, IMSMA database, etc. |
| 7.6 | Is the provision of IED risk education going to highlight the EORE operator as a provider of advice that is intended to counter the aims of parties to the conflict? | Again, this could result in the organization and its staff being considered as legitimate targets for attack by parties to the conflict. | Conflict analysis and risk assessment exercise. |
| 7.7 | What are the implications for the work of the other projects/programmes by the EORE operator? | Again, this could result in the organization and its staff being considered as legitimate targets for attack by parties to the conflict. | Conflict analysis and risk assessment exercise. |
| 7.8 | What are the risk implications for the national staff of the EORE operator? | National staff usually live and work in affected communities. Out of duty of care, it is necessary to be sure that provision of IED RE is not going to expose them to risk of retribution from parties to the conflict; or detention by state actors. | Conflict analysis and risk assessment exercise. |
| 7.9 | How can the risks for national staff be mitigated? | It is important to identify any precautions the EORE operator can take to avoid causing harm to national staff. | Conflict analysis and risk assessment exercise. |
| 7.10 | In cases where the EORE operator is already considered a target, will provision of IED RE incur significant additional risk? | In some working contexts, the EORE operator may already be considered a target. It is necessary to assess whether provision of IED RE will increase the likelihood of being attacked. | Conflict analysis and risk assessment exercise. |
D.3.2 What are the risk implications of participating in IED RE for members of the community?
| # | Question | Explanation | How can the question be answered? |
|---|---|---|---|
| 8.1 | How will community members participating in IED RE sessions be viewed by the government and security providers? | At community level, anyone who is known or suspected to have participated in an IED RE session could be viewed as a member of a party to the conflict by government and security providers so could be at risk of detention. | Engagement with local community leaders |
| 8.2 | How can we mitigate these risks? | It is important to identify any precautions the EORE operator can take to avoid causing harm to the local population at the hands of security providers. | Engagement with local community leaders |
| 8.3 | How will community members participating in IED RE sessions be viewed by parties to the conflict? | Who is known or suspected to have benefited from an IED RE session could be viewed as an informant by the parties to the conflict, so would be at risk of retaliation. | Engagement with local community leaders |
| 8.4 | How can we mitigate these risks? | It is important to identify any precautions the EORE operator can take to avoid causing harm to the local population at the hands of parties to the conflict and militias. | Engagement with local community leaders |
| 8.5 | How would asking people to report suspected IED be perceived by parties to the conflict? | In some countries, there may be widespread agreement among some communities with those placing the IED. In others, there may be a fear that retaliation will be taken against people reporting and/or marking IED. | Engagement with local community leaders |
| 8.6 | How would asking people to mark suspected IED be perceived by parties to the conflict? | In some countries, there may be widespread agreement among some communities with those placing the IED. In others, there may be a fear that retaliation will be taken against people reporting and/or marking IED. | Engagement with local community leaders |
Amendment record
Management of IMAS amendments
The IMAS series of standards are subject to formal review on a three-yearly basis. However, this does not preclude amendments being made within these three-year periods for reasons of operational safety and efficiency or for editorial purposes.
As amendments are made to this IMAS they are given a number. The date and general details of the amendment shown in the table below. The amendment is also shown on the cover page of the IMAS by the inclusion under the edition date of the phrase “incorporating amendment #.”
As the formal reviews of each IMAS are completed, new editions may be issued. In this case, amendments up to the date of the new edition are incorporated into the new edition and the amendment record table cleared. Recording of amendments then starts again until a further review is carried out.
The most recently amended IMAS are posted on the IMAS website at www.mineactionstandards.org.
| Number | Date | Amendment details |
Footnote
1 The Conflict Sensitivity Consortium, How to Guide Conflict Sensitivity, February 2012.
2 IMAS 07.14, Edition 1, Risk Management in Mine Action, Annex C, Threat Analysis and Threat Assessment in Environments Affected by Improvised Explosive Devices (IEDs).
3 Safe or safer? Communities at risk are likely to already have developed coping mechanisms to mitigate the existing risks but may need additional support to adopt safer behaviour. In addition, in some contexts, risk education contributes to reducing the risks but is not sufficient to guarantee the absence of risks.
4 For more details and examples, you can read the Behavioural Drivers Models, V. Petit, UNICEF.2019: www.unicef.org/mena/reports/behavioural-drivers-model
5 IMAS 05.10 Information management, Annex B Minimum Data requirements
